
AI CERTs
2 hours ago
EU Metadata Showdown Tests Communication AI
Europe’s push to combat child abuse online has returned, yet its latest draft carries broader consequences. Critics argue the Council’s Child Sexual Abuse Regulation (CSAR) risks cracking open WhatsApp’s end-to-end protections. Consequently, technologists warn that mandated metadata collection and client-side scanning create systemic vulnerabilities. Meanwhile, more than three billion users rely on WhatsApp for personal safety, activism, and business. Communication AI advances already shape how messages flow and how abuse is detected. However, forcing algorithms onto every device shifts that balance toward surveillance. Policy makers say new powers are essential after CyberTipline reports topped twenty million last year. Privacy defenders counter that scanning erodes trust and chills speech. This article unpacks the dispute, traces technical evidence, and outlines leadership actions.
EU Drafts Spark Concern
Denmark’s 2025 presidency circulated a revised CSAR text that removed explicit universal scanning. Nevertheless, it introduced “mitigation orders” and risk classes that effectively pressure encrypted platforms. Furthermore, the draft expands mandatory metadata retention and age verification. In contrast, earlier Parliament language defended strong Encryption as a fundamental right. Several member states now lobby for quick agreement before 2026 elections. Communication AI proponents within the Council believe device algorithms can reconcile safety and secrecy.
NCMEC received 20.5 million CyberTipline reports in 2024, down from 36.2 million a year earlier. Policymakers cite the decline as proof that hidden abuse migrates into encrypted channels. Therefore, they argue voluntary measures no longer suffice. Regulations supporters want binding obligations on high-risk services like WhatsApp.
These political maneuvers spotlight a high-stakes legislative chess match. However, final wording will decide whether Encryption remains intact.
Understanding metadata mechanics will clarify the technical stakes awaiting negotiators.
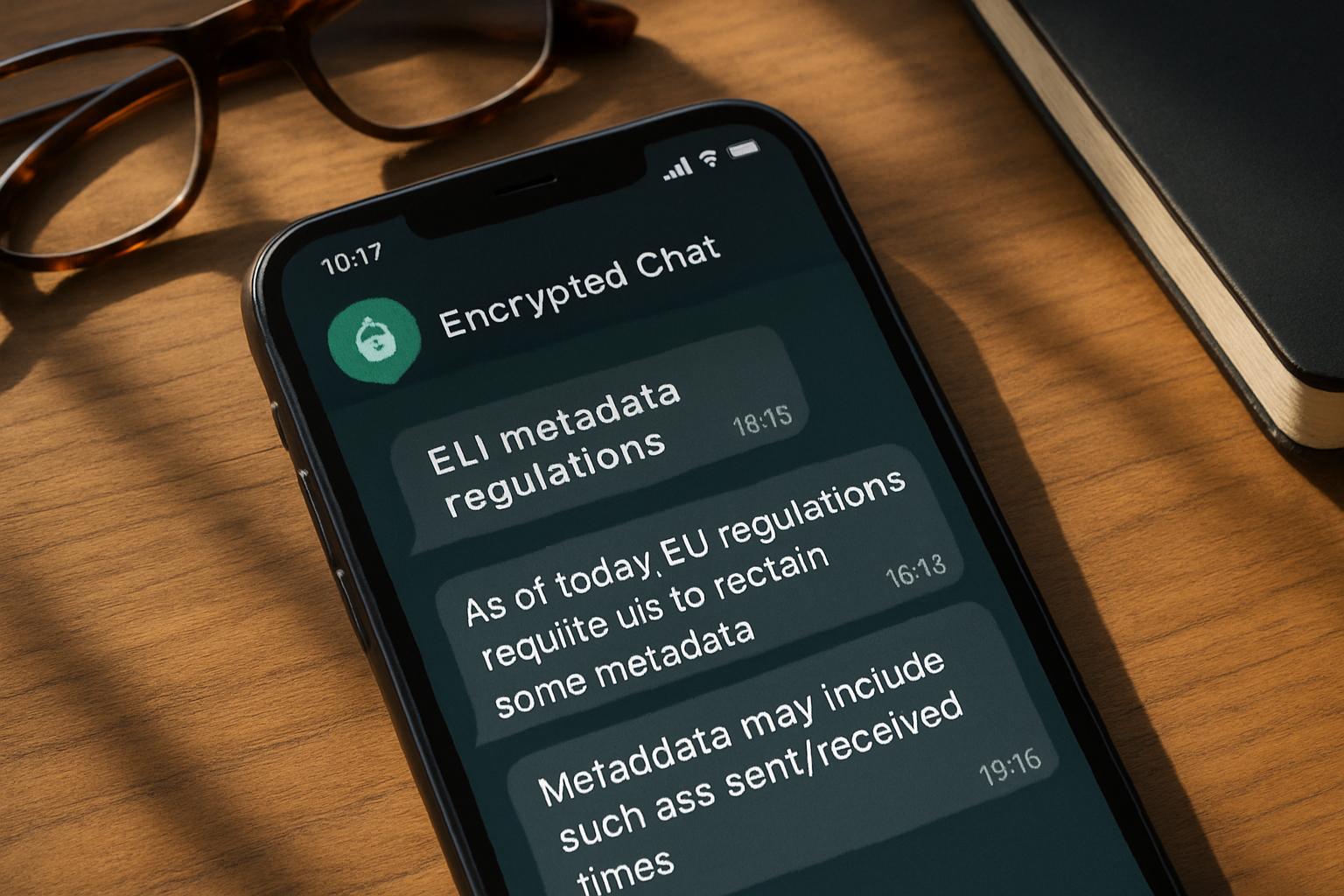
Metadata Rules Explained Clearly
Metadata describes who talks to whom, when, and from where—not message content itself. Yet traffic analysis of such data often reveals social networks, locations, and intentions. Moreover, retained identifiers enable Traceability requests from authorities long after messages vanish. WhatsApp already stores some routing logs for spam control, but expanded mandates would deepen those stores.
Client-side scanning amplifies exposure because code must view plain content before Encryption. Consequently, every endpoint becomes a potential surveillance sensor. Privacy experts compare the model to deploying billions of wiretaps. Communication AI models underpin these classifiers, and their false positives can overwhelm investigators.
Key metadata elements regulators target:
- Sender and recipient numbers, group IDs, and profile hashes
- Timestamps, IP addresses, and approximate locations
- Attachment sizes indicating possible illicit media
- Device fingerprints aiding Traceability
Expanded metadata capture widens investigative reach but simultaneously multiplies breach risk. Additionally, compulsory client scanning compromises device integrity.
The following section examines concrete engineering faults emerging from WhatsApp research.
Technical Risks For WhatsApp
Academic teams uncovered “Prekey Pogo” attacks that exhaust keys supporting forward secrecy. Therefore, adversaries can force fallback states lacking expected protections. Researchers also detailed backup injection schemes leaking conversation statistics.
Communication AI security reviews note that these exploits become easier if extra metadata is centralized for compliance. Moreover, mitigation orders could demand code paths that bypass established security checks.
Research Highlights Emerging Gaps
Injection tests in 2024 showed how manipulated backups reveal group sizes via differential message counts. Meanwhile, forced age-verification flows leak device biometrics. Privacy advocates warn such expansions create permanent attack surfaces.
Endpoints running mandated classifiers must maintain model updates and hash lists. Consequently, supply-chain attacks against those updates threaten billions.
Practical demonstrations confirm that even small protocol tweaks can cascade into systemic exposure. Nevertheless, many officials still view these issues as manageable engineering trade-offs.
Industry and civil resistance illustrates why that assumption faces mounting doubt.
Industry And Civil Pushback
Meta’s Will Cathcart warned the Council draft would “break encryption” and undermine global trust. Signal’s Meredith Whittaker echoed the message, stating that every new scanning avenue equals a fresh vulnerability. Furthermore, vendors like Threema threatened to exit European markets rather than comply.
Over 500 cryptographers signed open letters describing client-side scanning as technically infeasible. Civil society coalitions argue that Regulations erode fundamental rights, especially for journalists and marginalized groups. Meanwhile, the U.S. House banned WhatsApp on official devices, citing similar metadata worries, although for different jurisdictional reasons. Debate around Communication AI deployment standards widens this gulf.
Proponents reply that Traceability is necessary to locate abusers. However, opponents stress that broad dragnet powers historically spill into political surveillance.
The standoff pits safety narratives against security math. Consequently, compromise remains elusive.
Examining the legislative calendar helps leaders anticipate operational impacts.
Policy Timeline And Outlook
Trilogue negotiations start early 2026, with Germany and France holding swing votes. Coreper minutes from November 2025 suggest quick convergence on risk-based language. Additionally, Parliament rapporteurs push for sunset clauses and stronger oversight. Lawsuits questioning WhatsApp’s Encryption claims add further pressure. Stakeholders expect Communication AI compliance tools to emerge during transition periods.
Global spillover looms. In contrast, the UK and India monitor Brussels for precedents that could justify their own scanning mandates. Therefore, multinationals must prepare coordinated compliance and advocacy plans. Upcoming standards for Communication AI auditing will influence trilogue language.
Court challenges may delay enforcement yet cannot be the only hedge. Consequently, boards should assess data-retention architectures today, not after final votes.
Deadlines are tight, and text changes rapidly. Nevertheless, proactive technical mapping reduces scramble risks.
The next section outlines concrete steps leaders can adopt immediately.
Strategic Steps For Leaders
Boards should commission red-team reviews that test client code against CSS style threats. Furthermore, product teams must document existing metadata flows for future audit. Professionals can enhance their expertise with the AI Security Level-1™ certification.
Consequently, organizations should craft dual-track positions that defend Privacy while demonstrating voluntary safety investments. Communication AI governance committees can steer model deployment policies and logging limits. Moreover, transparency reports describing Traceability requests build credibility with regulators.
Immediate action checklist:
- Create a cross-functional Encryption task force within 30 days.
- Map metadata retention against proposed Regulations articles.
- Develop Communication AI abuse-detection pilots that respect on-device opt-ins.
Early planning positions companies as constructive actors, not reluctant holdouts. Therefore, preparation mitigates sudden compliance shocks.
The article concludes with key lessons and a call to action.
WhatsApp’s scale guarantees that any European shift reverberates worldwide. Policymakers chase necessary child-protection goals, yet proposed tools weaken Encryption and broaden metadata risks. Technical research shows that even limited client-side scanning undermines endpoint integrity. Meanwhile, civil society, industry, and cryptographers present a unified wall against compulsory measures. Communication AI will remain central to detection debates, but its deployment must respect fundamental Privacy and Traceability limits. Consequently, leaders need strategic clarity, robust engineering reviews, and proactive advocacy. Explore further guidance and skill up through recognized certifications, and stay ahead of evolving Regulations challenges.



