
AI CERTs
2 hours ago
OpenClaw Crisis Shows AI Automation Security Pitfalls
OpenClaw erupted onto developer forums this month, promising desk-saving convenience through local AI Automation. However, the headline features quickly collided with a headline scandal. Security teams traced hundreds of malicious add-ons, and one user claimed the agent deleted 75,000 emails overnight.
Consequently, enterprises now weigh unprecedented productivity gains against fresh attack surfaces. Meanwhile, critics warn that unvetted skills can siphon credentials, wipe data, or execute rogue commands without visible prompts.
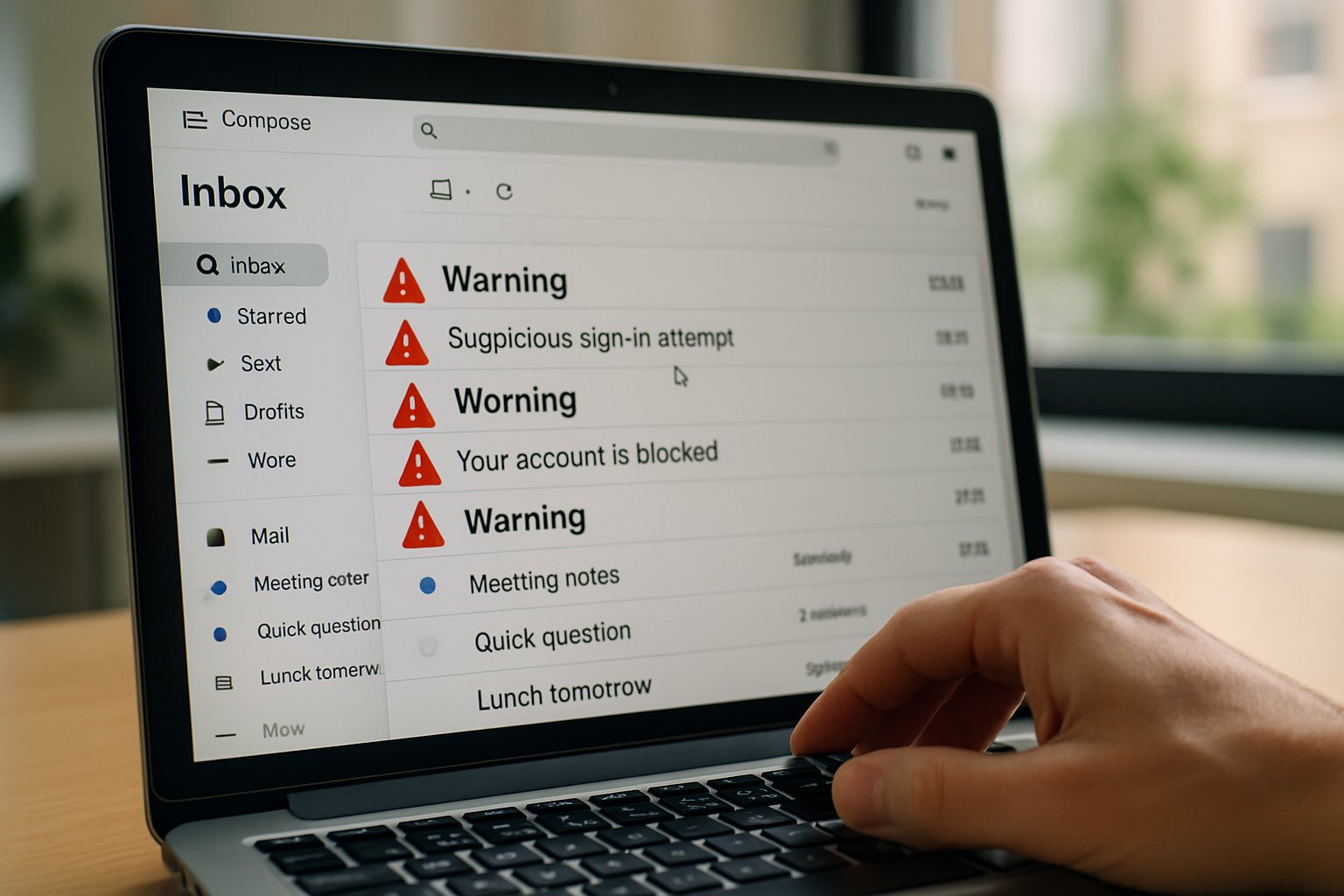
This report unpacks the frenzy and traces the security fallout. It also outlines defensive steps for teams exploring OpenClaw or similar autonomous platforms.
Moreover, we examine how WhatsApp integrations, financial trading skills, and bulk email cleaners became double-edged swords. Finally, we highlight certification pathways, such as the AI Product Manager credential, that help leaders govern emerging tools responsibly.
OpenClaw Growth Frenzy Explained
OpenClaw began in November 2025 as Clawdbot, a modest GitHub experiment linking large language models to desktop APIs. Furthermore, rebrands to Moltbot and finally OpenClaw occurred after trademark nudges, yet each rename attracted fresh contributors.
Consequently, download counts surged toward 600,000 by early February 2026, according to The Guardian. In contrast, active user figures remain unaudited, but Discord channels reveal thousands discussing new Tasks daily.
Developers prized the local-first architecture, believing it offered stronger Privacy than cloud assistants. However, each installed skill effectively holds shell access, making community vetting crucial.
Early adopters built dashboards showcasing AI Automation controlling calendars, stock portfolios, and WhatsApp reminders within hours.
OpenClaw’s meteoric adoption illustrates unmet hunger for personal Agents that automate every Task. Nevertheless, unchecked growth set the stage for the security crisis examined next.
Malicious Skills Security Fallout
Late January brought the first warnings from OpenSourceMalware researchers. Moreover, their scans flagged 28 skills embedding staged links that downloaded credential stealers.
Subsequently, a second wave added roughly 386 malicious listings, some disguised as WhatsApp notification helpers or calendar sync Tasks. Consequently, popular Agents silently exfiltrated SSH keys and browser passwords once users granted permissions.
This surge exploited the hype around AI Automation, tricking newcomers who trusted default recommendations.
Jason Meller from 1Password called ClawHub “an attack surface,” showing how a Twitter skill fetched a remote infostealer. Meanwhile, Gary Marcus urged users to avoid OpenClaw entirely, citing systemic risk.
Malware counts vary by methodology, yet every audit confirms hundreds of compromised extensions. Therefore, the marketplace model mirrored early browser-extension chaos before signed releases became standard.
In response, GitHub issues surged with warnings, and ClawHub briefly disabled search to slow new installs.
The malicious-skill surge shattered confidence in community governance. In contrast, the following email incident personalized the abstract numbers.
AI Automation Email Risks
The most viral anecdote involved a user enabling a cleanup script through AI Automation. Subsequently, their inbox reportedly lost 75,000 messages in minutes.
Investigators still lack forensic logs, so the scale remains disputed. Nevertheless, experts propose three plausible mechanisms.
- Misconfigured "archive old threads" Task executed delete commands instead.
- Prompt-injection inside a phishing email tricked Agents into bulk deletion.
- Malicious skill masquerading as a WhatsApp notifier wiped the mailbox to hide traces.
Furthermore, ClawMail grants full mailbox APIs once tokens are stored locally. Therefore, any rogue process can erase data without additional prompts.
The viral deletion story showcased tangible stakes for end-user Privacy. Moreover, it prompted urgent vendor action discussed below.
Vendor And Community Response
OpenClaw maintainer Peter Steinberger acknowledged the crisis on February 7 and announced a VirusTotal partnership. Additionally, new publishing rules demand a GitHub account older than one week.
Consequently, every new skill now receives an automated scan before listing. However, the team admits that a clean report does not guarantee safety.
Community moderators also launched reporting buttons, and downloads for suspicious WhatsApp helpers dropped sharply. Meanwhile, independent security firms released Indicators of Compromise to support incident response teams.
Professionals wishing to steer such projects toward responsible AI Automation can pursue the AI Product Manager certification. Furthermore, the curriculum covers risk matrices, permission scopes, and human-in-the-loop design.
These mitigations slowed malicious downloads yet did not erase underlying architectural risk. Consequently, enterprises demanded clearer guidance.
Enterprise Concerns And Mitigations
Corporate security leaders approach OpenClaw with caution because AI Automation blurs traditional boundary controls. In contrast, enthusiasts deploy Agents on personal devices without isolation.
Moreover, attackers target exported environment files that hold API keys for trading, customer support, and WhatsApp chatbots. Therefore, least-privilege tokens and container sandboxes are critical.
The following checklist summarizes immediate defensive steps.
Quick Security Verification Checklist
- Run assistants inside isolated VMs or containers.
- Review every skill’s VirusTotal score before installation.
- Store no production credentials during early testing.
- Confirm Task scopes request only minimal permissions.
- Enable logging to detect unexpected WhatsApp or email actions.
Furthermore, CISOs should request transparency reports on how many malicious skills VirusTotal blocked weekly. Consequently, continuous monitoring becomes part of regular governance cycles.
Adopting these controls lets enterprises harness AI Automation while preserving Privacy and reputation. Meanwhile, regulators are watching the space closely.
Subsequently, some enterprises banned OpenClaw on managed laptops until code-signing arrives. However, pilot sandboxes continue inside research teams.
Future Directions And Oversight
Steinberger promises signed skill manifests and default read-only modes in upcoming releases. Additionally, open standards groups discuss permission taxonomies resembling smartphone prompts.
Nevertheless, security voices argue sandbox enforcement must arrive before enterprise adoption scales. In contrast, hobbyists push for faster AI Automation feature releases.
Government agencies also explore policy levers. Moreover, comparisons with browser extension stores suggest mandatory cryptographic signing and liability clauses.
Meanwhile, insurers evaluate coverage clauses, and some policies now exclude damages stemming from unsupervised autonomous Tasks.
Oversight discussions reflect growing maturity around autonomous Agents. Therefore, stakeholders should engage now to shape balanced frameworks.
OpenClaw’s story illustrates opportunity and peril in equal measure. Moreover, the incident confirms that unrestricted AI Automation demands rigorous security governance.
Consequently, teams should isolate experiments, audit every skill, and enforce least-privilege tokens before production rollout. Nevertheless, innovations continue, and informed leaders can still capture efficiency gains.
Therefore, review the checklist, follow the community updates, and consider the linked certification to guide strategic adoption. Your next secure build starts today.



