
AI CERTS
2 hours ago
OAuth Phishing Elevates Cybersecurity Risk Through 2026
Consequently, readers gain practical guidance to defend Microsoft 365 and similar platforms. Proofpoint, Datadog, and Microsoft supply the validated evidence referenced here. Moreover, statistics reveal campaigns affecting thousands of tenants and millions of messages. Finally, we link to the AI Security Compliance certification for deeper specialization. Nevertheless, defenders can still outpace adversaries by tightening consent policies and blocking risky flows.
Identity Threat Landscape 2026
Recent telemetry illustrates a steep spike in OAuth consent abuse since mid-2025. Proofpoint counted multiple clusters exploiting device-code flows against Microsoft 365 tenants. Meanwhile, RH-ISAC summarized attacks touching 900 tenants and 3,000 user accounts. Consequently, identity compromise now ranks among the highest Cybersecurity Risk vectors for enterprises. OAuth tokens persist beyond password resets, providing attackers quiet, durable access. Furthermore, one 2023 campaign created 17,000 malicious apps and sent 927,000 messages. These numbers underscore scale impossible with classic credential phishing alone. In contrast, consent screens appear on trusted domains, tricking even security-savvy users. Therefore, defenders must shift focus from email payloads to token governance.
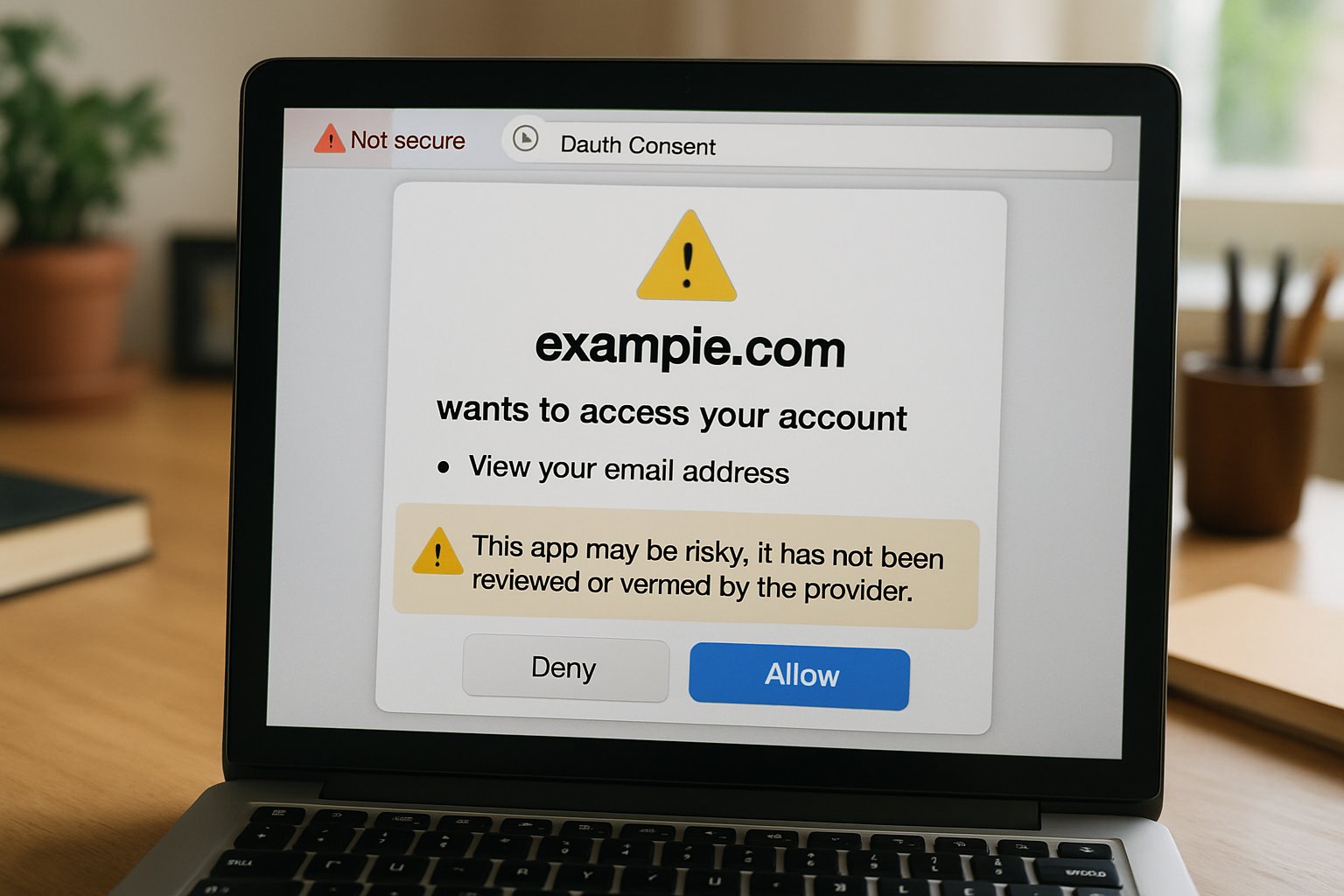
The landscape reveals volume, persistence, and trust abuse. Next, we examine the five priority threats shaping 2026.
Five Priority Threats Ahead
Researchers highlight five OAuth-centric perils demanding attention through 2026. Firstly, device-code phishing scales quickly with QR or short-code lures.
- Device-code campaigns abuse Microsoft legit pages, evading traditional filtering.
- Platform-hosted consent abuse, such as CoPhish, leverages trusted domains for higher success.
- Commodity kits like Graphish lower skills required, boosting attack volume.
- Admin-consent impersonation exploits verified publisher trust, expanding reach.
- Token persistence fuels automation, including internal spam and business fraud.
Moreover, each threat intersects with existing cybercrime ecosystems, compounding damage. Collectively, they elevate Cybersecurity Risk for cloud identity fabrics.
These five vectors demand immediate prioritization in roadmaps. However, understanding the tooling behind them clarifies defense strategies.
Emerging Attack Toolkits 2026
Tool availability shapes attacker economics more than raw discovery. SquarePhish, SquarePhish2, Graphish, Tycoon, and ODx automate complex OAuth sequences. Subsequently, less skilled actors join campaigns, widening cybercrime participation. Proofpoint observed these kits driving half the device-code traffic during autumn 2025. Additionally, Datadog reported CoPhish weaponizing Copilot Studio agents for stealth exfiltration. Graphish even offers a subscription service with support channels and regular updates. Consequently, toolkits multiply Cybersecurity Risk by scaling speed and consistency. Defenders must monitor known kit fingerprints, such as unique app IDs and redirect URIs. Nevertheless, detection alone is insufficient without proactive policy blocks.
Automated kits transform niche exploits into mainstream threats. The following section outlines actionable mitigations to counter this surge.
Mitigation Tactics Checklist Guide
Multiple vendors now publish concrete defensive steps. Therefore, organizations should build a layered checklist covering quick wins and strategic goals.
- Block device-code flows where feasible using Conditional Access controls.
- Require admin consent for all high-risk scopes and unknown publishers.
- Deploy phishing-resistant MFA, preferably FIDO2 keys, for privileged roles.
- Audit OAuth apps weekly, revoking dormant entries and suspect tokens.
- Monitor unusual app creations and API calls via Entra logs.
Moreover, professionals can deepen knowledge through the AI Security Compliance™ certification. Applying these measures lowers Cybersecurity Risk while preserving operational continuity. Consequently, help-desk friction stays manageable compared to breach response costs.
The checklist targets immediate attack surfaces. In contrast, broader policy shifts address the usability debate next.
Balancing Usability And Security
Blocking entire OAuth flows can disrupt legitimate device onboarding and IoT integrations. However, vendors argue that selective restrictions outweigh downtime from token abuse. RFC 8628 highlights the original usability rationale for the device authorization grant. Microsoft and Okta therefore push tenant configurations that minimize user consent exposure. Meanwhile, critics warn aggressive controls may slow service adoption, hurting innovation. Nevertheless, cybercrime economics favor defenders who raise attacker cost through governance. Organizations must quantify Cybersecurity Risk against productivity before deploying blanket blocks.
Proper analysis aligns security investments with business objectives. Subsequently, governance emerges as the decisive lever.
Strategic Governance Moves Forward
Strategic moves embed security into procurement, architecture, and culture. Firstly, establish an application allowlist process linked to change management. Secondly, integrate third-party risk reviews for every new cloud service. Thirdly, publish a consent exception policy that documents business justification and expiry. Moreover, automate alerting for suspicious grants using SIEM playbooks. Consequently, leadership gains continuous insight into Cybersecurity Risk exposure. Annual tabletop exercises should test token fraud scenarios and containment. Meanwhile, partnerships with ISACs provide timely indicators and peer benchmarks. Finally, boards must receive metrics tying fraud losses to governance gaps.
Strong governance transforms piecemeal controls into sustained resilience. Therefore, the journey concludes with clear next steps for readers.
OAuth token abuse now sits at the heart of modern Cybersecurity Risk calculations. Device-code phishing, trusted-domain consent phishing, and toolkit automation will persist through 2026. However, organizations that follow the checklist can shrink Cybersecurity Risk while maintaining vital service continuity. Governance, admin consent, and resilient MFA also reduce fraud and broader cybercrime exposure. Consequently, teams gain bandwidth to innovate rather than remediate. Professionals seeking deeper mastery should pursue the linked certification to reinforce Cybersecurity Risk management skills. Act now, update policies, and test defenses before attackers test you.



