
AI CERTS
3 months ago
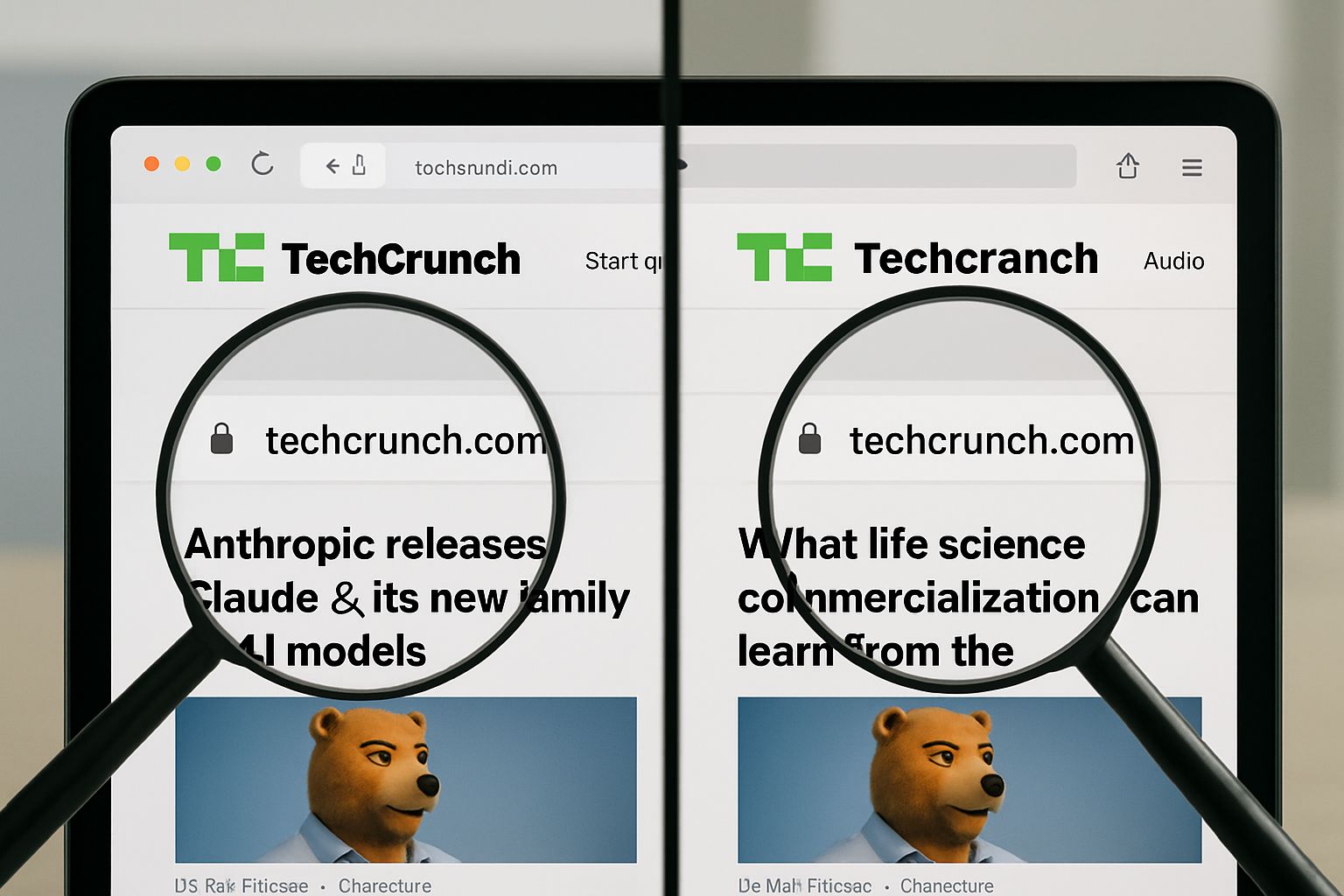
Inside TechCrunch Phishing Campaign Impersonating Reporters
This article unpacks the threat, examines tactics, and shares countermeasures for busy security leads. Moreover, we verify claims through TechCrunch advisories, FBI crime data, and vendor telemetry. Readers will also discover professional upskilling paths, including an AI marketing certification that strengthens organizational resilience.
Meanwhile, brand-impersonation schemes are scaling because phishing-as-a-service kits lower technical barriers. In contrast, defenders often struggle with fragmented verification workflows and rushed media deadlines. Therefore, understanding the anatomy of the hoax becomes crucial for communications teams and executive stakeholders alike. This report maintains concise sentences to maximise clarity for technical audiences. Hackers exploit Reporter Mimicry to build trust quickly.
Rising Threat Landscape
Brand impersonation surged 33% year-over-year, according to the FBI IC3 2024 report. Furthermore, phishing and spoofing complaints exceeded 193,000, with reported losses touching $70 million. Check Point Research found technology brands made up the most imitated category during Q2 2025, at 45% share. Moreover, Microsoft alone represented one quarter of brand-phishing observed. The TechCrunch impersonation wave fits this wider arc. Threat analysts link the activity to a persistent actor leveraging commoditized infrastructure. Consequently, organisations face an ongoing, adaptive Phishing Campaign that evades simple blocklists.
The statistics confirm a persistent, expanding threat surface. However, understanding specific tactics provides sharper defensive focus.
Growth Behind Numbers
Several discrete metrics illustrate the momentum behind brand impersonation. Additionally, they expose financial incentives motivating copycat domains.
- FBI IC3: $16.6 billion total cyber losses during 2024, up 33%.
- Phishing/spoofing complaints: 193,407, reflecting steady annual growth.
- BEC losses: $2.77 billion, often initiated by spoofed outreach.
- Microsoft seizure: 340 domains tied to Raccoon0365 service.
- Check Point: Technology brands made up 45% of Q2 2025 phishing.
These numbers signal industrialised phishing economics. Consequently, attackers can fund rapid infrastructure replacement when domains get seized. Next, we unpack the social-engineering playbook behind the TechCrunch spoof. The current Phishing Campaign volume dwarfs last decade's totals.
Impersonation Tactics Explored
Attackers register Lookalike Domains that resemble authentic TechCrunch addresses, adding hyphens or alternate TLDs. Moreover, they copy official reporter biographies, ensuring linguistic style and signature blocks feel legitimate. Every email within the Phishing Campaign mimics internal newsroom formats down to signature glyphs. Malicious emails request comment on breaking stories or propose interview slots. Subsequently, calendar links route victims to credential-harvesting portals or voice calls designed to pressure disclosure. Reporter Mimicry peaks when attackers cite recent TechCrunch articles, creating believable context. In contrast, generic spam lacks such topical anchors and triggers quicker suspicion. Notably, the actor alternates channels, shifting from email to voicemail or encrypted chat when defenders question legitimacy.
The tactics blend technical deception with tailored conversation hooks. Therefore, defenders must address both infrastructure filtering and human verification workflows. The human cost of these ruses becomes clear in victim impact data.
Reporter Mimicry Methods
Threat actors study public speaker videos to replicate cadence during follow-up calls. Additionally, they schedule interviews outside normal hours, limiting opportunity for internal cross-checks. Emails often embed subtle grammatical quirks copied from genuine TechCrunch reporting. Nevertheless, slight timezone mismatches and odd logo placements remain tell-tale anomalies. Security teams can train staff to highlight these micro signals during content review.
Reporter Mimicry succeeds because busy staff default to trust. However, consistent style guides and verification scripts can expose counterfeit pitches quickly. Understanding organisational fallout underscores why such controls matter.
Impact On Tech Firms
Credential theft facilitates account takeover, lateral movement, and potentially catastrophic data exposure. Consequently, startups negotiating funding rounds risk leaks that jeopardise valuations. Proofpoint ties many cloud ransomware intrusions to initial brand spoof emails similar to this threat. Meanwhile, PR managers lose hours sorting fraudulent requests, delaying genuine coverage opportunities. Lookalike Domains also dilute domain reputation, triggering false positive blocks against real media. Security chiefs report increased MFA push fatigue as attackers repeatedly test stolen credentials.
The operational impact stretches beyond immediate dollars lost. Therefore, leadership must view prevention as brand protection, not mere technical hygiene. Effective controls begin with layered, human-centric defences. A single successful Phishing Campaign can trigger cascading reputational damage that outlives immediate recovery costs.
Defensive Best Practices
Organisations should compile known malicious TechCrunch domains and block them at the gateway. Additionally, implement banner warnings on external emails to flag potential spoofing attempts. Enforcing phishing-resistant multi-factor authentication stops session theft even when passwords leak. Moreover, SIEM rules detecting unusual employment-related keywords from new domains can surface attacks earlier. Communications teams need a simple verification checklist.
- Confirm sender identity through TechCrunch staff directory.
- Cross-check Lookalike Domains for extra characters.
- Call listed newsroom phone numbers before sharing files.
- Avoid clicking scheduling links until verification completes.
Professionals can expand expertise via the AI Marketing Strategist™ certification. Furthermore, periodic tabletop exercises reinforce response playbooks and clarify communication channels.
Layered controls reduce risk exposure dramatically. Nevertheless, no filter replaces disciplined human verification. Collaboration across industry lines supplements these internal measures. Blocking one Phishing Campaign instance today prevents countless downstream credential abuse attempts tomorrow.
Industry Collaboration Efforts
Microsoft, Cloudflare, and law enforcement seized 340 domains tied to Raccoon0365 operators. Consequently, takedowns disrupt infrastructure yet attackers respawn within hours using new registrars. TechCrunch continues publishing updated domain lists, urging readers to share indicators. Additionally, vendors exchange telemetry through threat intelligence platforms, accelerating blocklist distribution. Industry alliances also lobby registries for tighter identity checks before approving suspicious names.
Joint action hampers attacker scale, though cannot fully eradicate abuse. In contrast, proactive company defences remain the final barrier protecting assets. Anticipating attacker innovation informs the next strategic move. Shared intelligence lets defenders trace the Phishing Campaign infrastructure and pre-empt domain purchases.
Future Risk Outlook
Generative AI tools already craft highly personalised emails, expanding future attack potential. Moreover, deepfake voice technology could enhance Reporter Mimicry during phone interviews. Lookalike Domains may soon integrate homograph characters, complicating visual inspection. Therefore, domain protection services and Unicode blocking lists gain importance. CISO leaders should budget for continuous awareness training and automated abuse monitoring. Meanwhile, regulators may mandate verification steps for third-party outreach, raising compliance stakes. The Phishing Campaign threat surface will likely widen as commoditised kits grow cheaper.
Preparation now limits costly surprises later. Consequently, agile risk governance pays dividends when new lures emerge.
Organizations cannot ignore the evolving Phishing Campaign wave impersonating trusted newsrooms. Nevertheless, disciplined verification, layered controls, and timely intelligence sharing sharply reduce exposure. Moreover, this specific Phishing Campaign highlights how human relationships remain prime attack vectors despite technical safeguards. Continual awareness training equips staff to detect Reporter Mimicry and scrutinize Lookalike Domains under pressure. Consequently, boards should fund regular simulations and reward prompt reporting of suspicious outreach. Professionals seeking deeper strategic insight can pursue the AI Marketing Strategist™ certification. By uniting skilled teams, smart tools, and cooperation, companies can keep tomorrow's imposter emails at bay.



